
NEW: Uncover the Latest Cyber Threats!
Stay ahead of evolving cyber threats. Download the H1 2025 Cyberseer SOC Threat Findings Report for insights on AiTM phishing, malware persistence, and more.
Ransomware continues to cast a long shadow over the digital security of businesses around the world. The increasing number of cyberattacks is a stark reminder that we must all prepare for the evolution of these threats. As we’ve seen over recent years, this type of criminal activity has grown from simple extortion to multifaceted attacks that leverage data theft and compliance pressures.
Ransomware victim numbers rose by 50% in 2023.”
Over 500,000 new cyber threats are discovered every day, and of those that are attacked a growing proportion are small to medium-sized businesses.
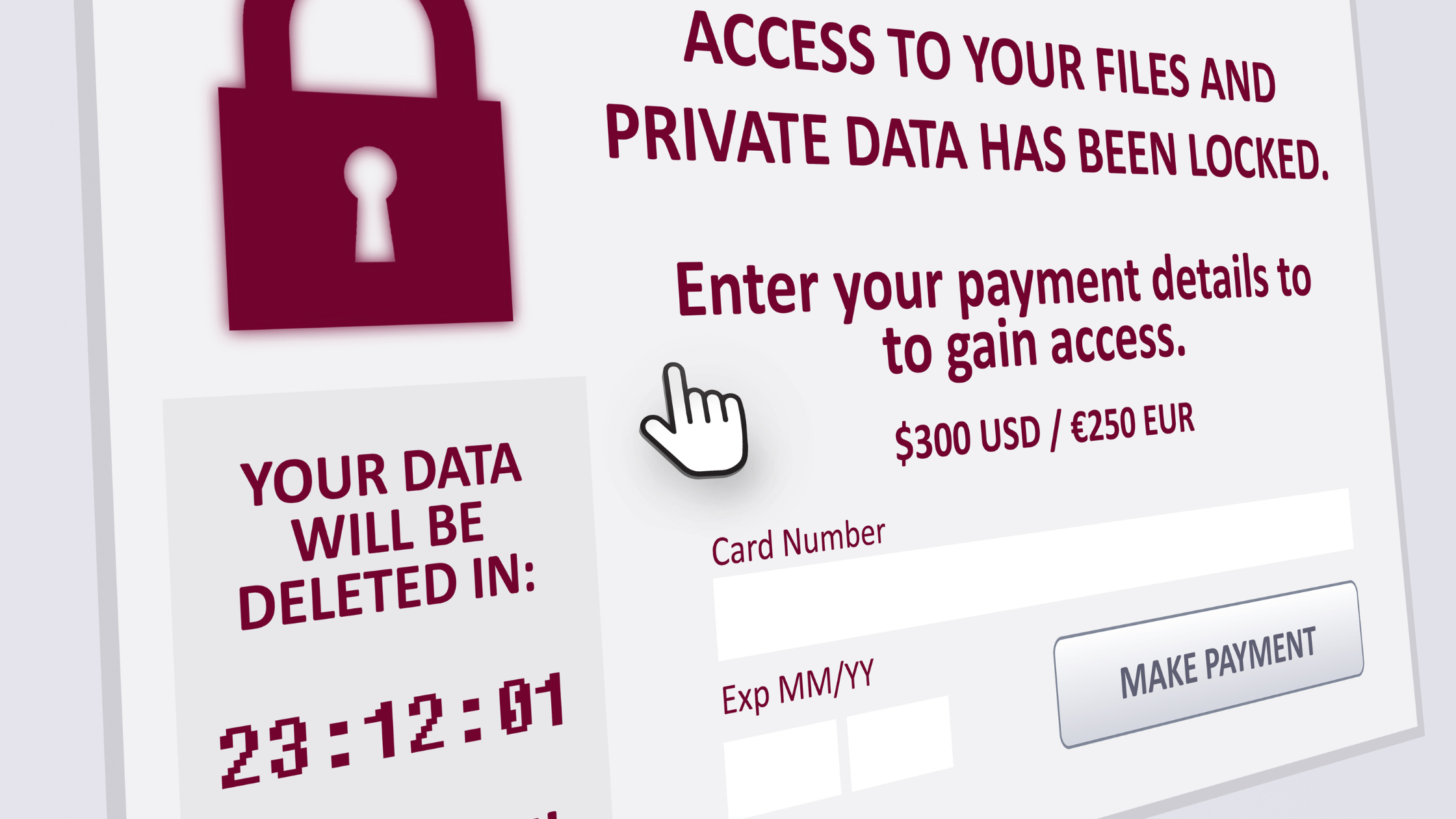
Ransomware is a type of malicious software, also known as malware, designed to restrict or completely block access to a computer system until a sum of money is paid. Modern ransomware tactics may include the theft of an organisation’s customer data that could also be used to launch additional fraud attacks. This means that a single attack has the capacity to add additional threat layers to corporate security.
If you know your system has been infiltrated by ransomware, it’s already too late!”
The manufacturing sector is one of the most targeted industries by cyber criminals and accounts for 14% of data leak incidents. Professional services, retail, construction, high-tech, healthcare, financial services, and education sectors are also regularly targeted due to the potential amount of sensitive data that they hold.
Geographically, it’s been the affluent regions of the UK, US, Canada, Germany and France that have been seen as prime targets due to their economic activity.
6.5% of all ransomware victims are located in the UK.”
The trend, so far, has been to attack English-speaking countries with phishing attacks. However, now that AI can create authentic-sounding emails in a variety of languages, without the tell-tale signs of poor spelling and grammar, the criminal net has been widened.
There are two main ransomware categories: Locker Ransomware, which denies access to system functions, and Crypto Ransomware, which encrypts files, rendering them inaccessible.
Subsets of these include:
Ransomware can often be inserted into a network via a ‘phishing attack’. This is often caused when the recipient is tricked into clicking on a link or entering information that allows a piece of malware to be covertly downloaded. That malware is then able to ‘infect’ the computers that it has access to, spreading quickly and often silently through an entire organisation. The cybercriminals behind the attack will then offer to decrypt your data in exchange for a hefty ransom. They usually ask for a ransom payment to be made via cryptocurrency as it is much more difficult to trace.
However, it’s Ransomware-as-a-Service (RaaS) that is causing significant concern. The sophisticated attack capabilities of this model allow less skilled cybercriminals to launch ransomware attacks. As it removes the coding knowledge barrier, it’s easy to understand how the RaaS model has enabled an upsurge in ransomware attacks. It’s marketed as a full-service offering that can include monthly subscriptions, tracking of infection and payment status, different revenue models plus a 24/7 support service for paying cybercriminal customers.
Criminals can ratchet up the pressure on a victim to pay the ransom by using ‘Double extortion’ which not only holds an organisation to ransom but also exfiltrates the victim’s data. This provides cybercriminals further leverage in negotiations by threatening to release the data into the public domain.
As ransomware attacks become more sophisticated, we predict an increase in assaults on SaaS platforms, leaving cloud-based solutions particularly vulnerable. Businesses must prioritise multifactor authentication (MFA) strategies and reinforce their security training for all employees.
Another trend, first identified in 2013 and known as ‘Living-off-the-Land’ (LOTL), is a technique that infiltrates a user’s system and uses legitimate tools already present to deliver an attack. Traditional malware attacks rely on files injected into the user’s system; LOTL attacks are file-less. Tools and files such as CertUtil, Regsvr32, schtasks, PowerShell and Windows Management Instrumentation (WMI) can all be used in this form of ransomware.
97% of businesses that fall victim to a cyberattack could have been protected if they had robust cybersecurity monitoring solutions or Endpoint Detection & Response (EDR) in place.
To safeguard against ransomware, companies should establish comprehensive cybersecurity programs that go further than firewalls, EDR, encryption, backups, access control and employee training. Compliance with data breach notification laws, such as GDPR, is also critical to maintaining regulatory integrity Importantly though, there should be a clear strategy to cover automated responses, network segmentation, zero trust, testing specific responses and recovery playbooks.
To a degree, all businesses should expect to become targets of cybercrime at one time or another. And although this might sound defeatist, it’s actually a call to arms. Implementing egress rules to prevent suspicious web traffic and employing geo-blocking can significantly mitigate the risks. But more can be done.
AI and large-language-model algorithms continue to evolve and present increased opportunities for cybercriminals. However, the flip side is that AI can be used to help protect business cyber defences too.
It’s not just large corporations at risk; smaller businesses are increasingly under threat as they seek to tighten budgets. The cybersecurity skills shortage makes it difficult to retain top talent in-house. Ensuring you have access to the highly trained experts at Cyberseer is a simple cost-effective solution that prevents the need to constantly recruit and attempt to retain your security staff.
As ransomware’s capabilities grow, so too must our resilience. By staying informed, remaining vigilant, and implementing tough cybersecurity measures, businesses of all sizes can navigate the ransomware threat landscape.
Learn more about our Managed Security Services and how we keep your data, systems and reputation safe.
Sources:
Action Fraud
Palo Alto Networks
CSO online

Stay ahead of evolving cyber threats. Download the H1 2025 Cyberseer SOC Threat Findings Report for insights on AiTM phishing, malware persistence, and more.