
NEW: Uncover the Latest Cyber Threats!
Stay ahead of evolving cyber threats. Download the H1 2025 Cyberseer SOC Threat Findings Report for insights on AiTM phishing, malware persistence, and more.
Google Security Operations is a new threat-hunting platform, developed by Google. Leveraging Google, Cloud and Threat Feed technologies it provides analysts with the ability to deep dive into accessible and enriched logs.
It gives companies 12 months of hot storage with sub-second searchability. It gives Google Search to the security industry. Basic SoC queries such as “How many devices accessed this IP address in the past 12 months” can now be answered with the click of your fingers and this is something the cybersecurity industry hasn’t really seen before.
While that is a feat in itself Google Security Operations takes this further; it takes IOC (Indicator of Compromise) feeds from multiple sources (including Government agencies and VirusTotal) and can apply this to the data it ingests.
All ingested data gets indexed so Google Security Operations will automatically retro-search the indexed data every time it sees a new IOC.
This means there’s truly nowhere to hide for malicious actors; the moment they are on the radar an analyst can quickly pivot off this information to provide a detailed timeline of when an environment became first infected and all the other devices involved.
This provides you 100% coverage from those ‘low and slow’ types of infections. Google Security Operations presents this data in such a way that the analyst gets a comprehensive view of what happened before and after, from all log sources ingested into the platform.
Well-thought-out visualisation of this data makes it easy to identify interesting patterns of behaviours:
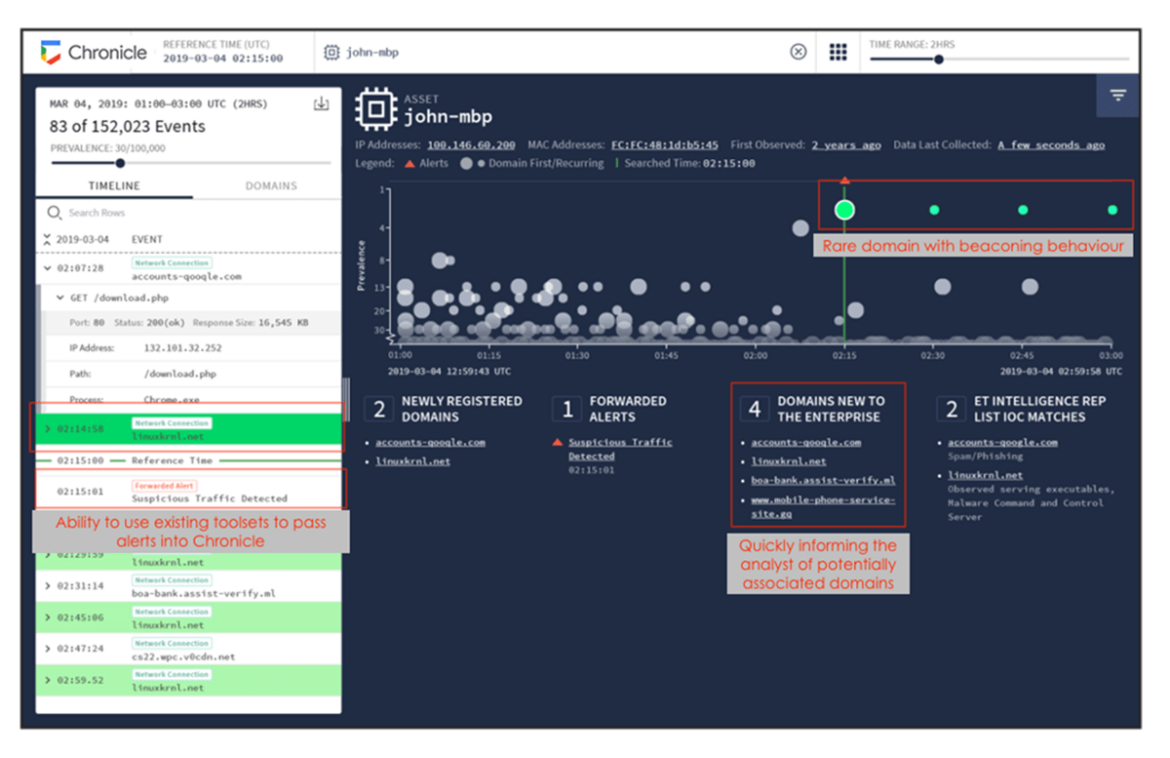
In the screenshot above it’s clear to see all that in action. In one simple view, we can see a rare domain, the process that interacted with it and then clear beaconing activity; streamlining an analyst workflow. As for what data can be consumed by the platform, Google Security Operations made it clear that it just needs to be a security-related log.
All Google Security Operations Platform needs to do is index the data and if it can’t do that straight away the Google Security Operations team will support the end user to get their data ingested onto the platform. This functionality is then added to the product, meaning everybody gets the benefit. Even in its infancy Google Security Operations can take in DHCP, DNS, Proxy and EDR.
The impressive speed allows analysts to search petabytes of data in seconds. The impressiveness isn't just limited to data search but extends to the ingestion too as Google Security Operations can rapidly scale out dynamically across Google’s existing cloud platform. Log collection is simple too, adopting a containerised approach with multiple ingestion methods.
On a techie front Google Security Operations are solving ingestion issues commonly seen in SIEM projects by use of UDM (Unified Data Model). This is a predefined list of Google Security Operations fields to help Google Security Operations best understand the different data types it’s ingesting. Having such clear standards fields of ingested data has allowed Google Security Operations to work hard on its biggest playing card; YARA-L.
YARA-L … and why we’re excited!
‘YARA’ may be a term familiar to the security community. It’s a known standard for writing detection rules in. The key word here is community. Understanding the rule syntax and not having to learn anything new means that SoC teams and MSSPs will be able to put effective detection rules straight in with very little modification. Google Security Operations has taken this one step further by actively working with the security community to provide conversion tools from other rule formats.
Why is this important? A community rule to identify a new zero-day attack could be applied in a matter of minutes. You then only need to add a couple of seconds to this to search your past 12 months of data for any indicators of compromise. Streamlining at a new level.
The familiar syntax for rules also covers the other SIEM problem … noise. This makes it easier for an analyst to change the conditions of rules so that there is more accurate detection within rules. Google Security Operations is constantly improving the syntax too, with planned additions for device lists within rules, and different network groups. This could be great for those devices that you want extra insight and monitoring of.
While we’re talking security, if you’ve already got existing solutions, Google Security Operations can also consume feeds from these giving businesses the freedom to migrate to the cloud or augment with their existing SIEMs.
12 months minimum, sub-second query responses across entire log data sets, clean informative presentation of data will all associated contextual data on hand. All are scalable and readily available in the cloud.

Stay ahead of evolving cyber threats. Download the H1 2025 Cyberseer SOC Threat Findings Report for insights on AiTM phishing, malware persistence, and more.