
NEW: Uncover the Latest Cyber Threats!
Stay ahead of evolving cyber threats. Download the H1 2025 Cyberseer SOC Threat Findings Report for insights on AiTM phishing, malware persistence, and more.
In the rapidly evolving cybersecurity landscape, having robust investigative capabilities is paramount for businesses to swiftly detect, respond to, and mitigate threats effectively. Microsoft Defender for Endpoint, a cutting-edge EDR solution, stands at the forefront of this battle, equipping security teams with investigative capabilities to uncover and neutralise threats with unprecedented accuracy.
In this blog post, we delve into real incidents observed by Cyberseer in customer environments, showcasing how Microsoft Defender for Endpoint’s insights expedited response times within its native Microsoft Security portal as well as when sending raw telemetry and alert information into other security toolsets.
Phishing and Malspam continue to plague organisations worldwide, manifesting as malicious links within emails to various fake login portals and Adversary in the Middle (AiTM) toolkits, or malevolent attachments. Cyberseer has observed detections for all variations of these attacks.
Microsoft Defender for Endpoint furnishes Analysts with critical threat information, including involved assets, users and artefacts. Visual graphing is then used to show the connections between these pieces of information aiding in the scope of an attack. The screenshot below demonstrates the detection of a malicious attachment:
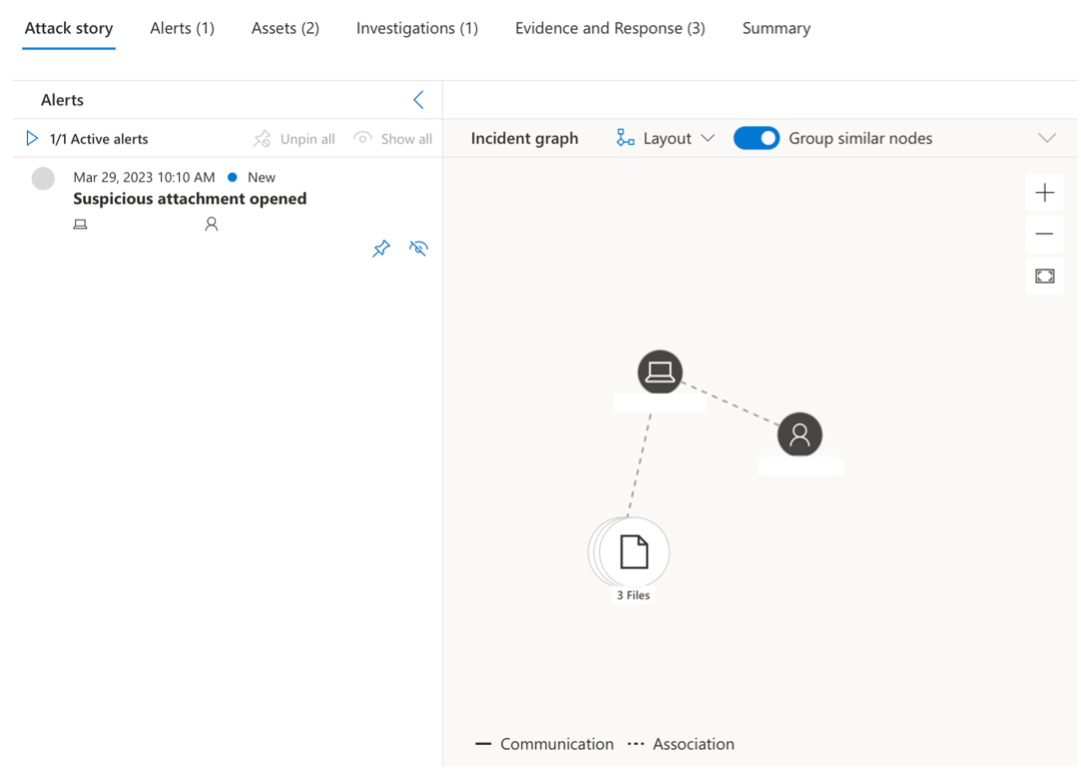
Further analysis reveals the process tree of the detection.
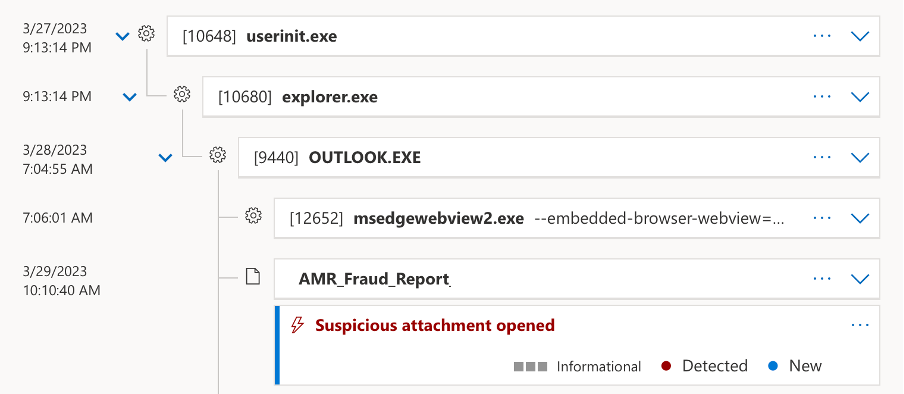
By tracking back and reviewing the ‘OUTLOOK.EXE’ process, we can easily see that a malicious document file download was responsible for triggering the alert.
In a perfect world, an organisation would have full control over user devices and defined security boundaries. However, threats can infiltrate via unconventional means like user-owned USB devices or unsanctioned applications. Two incidents observed by Cyberseer exemplify this.
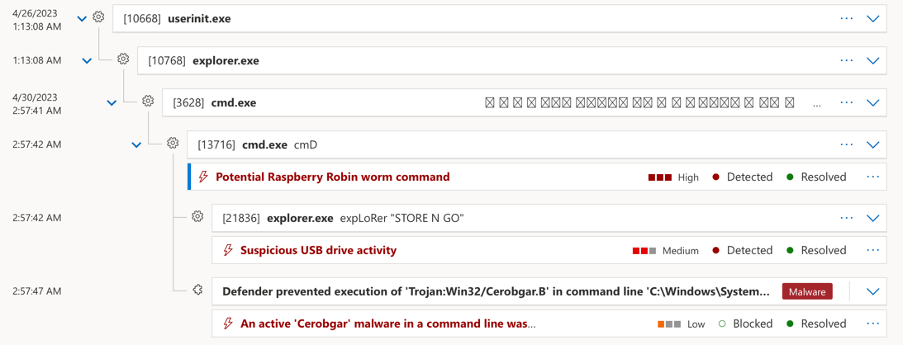
The first is the ‘Raspberry Robin’ worm which is propagated via external storage devices:
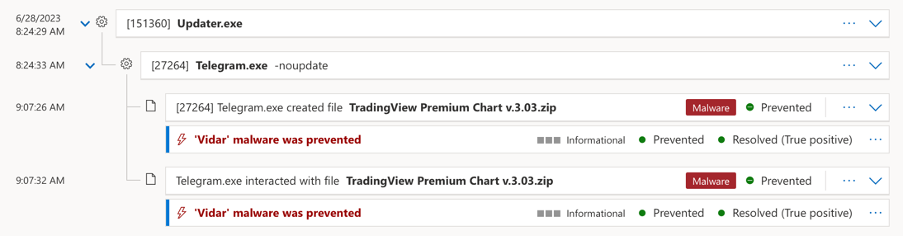
The second incident highlights the exploitation of the popular chat application ‘Telegram’, to disseminate malicious files. Cyberseer has observed malicious files being downloaded from group chats:
Unsanctioned applications introduce two critical scenarios organisations must consider. Firstly, they provide an additional vector for malware to infiltrate an environment, and secondly, they provide a pathway for data exfiltration to leave an environment.
As cyber threats continue to evolve, robust security strategies are imperative. Microsoft Defender for Endpoint’s integration with other security tools amplifies its capabilities, providing an all-encompassing defence against sophisticated threats. For further insights, check out our blog post titled “Collaborative Defence: Advancing Microsoft Defender with Integrated Security Tools.” Through the synergy harnessed by Cyberseer, proactive and efficient threat mitigation is achieved, preserving businesses' safety and reputation in an increasingly treacherous digital landscape.

Microsoft Defender for Endpoint (MDE) combines anomaly-based detection, deterministic countermeasures, and automated response in a single modern interface to cover all tactics of the MITRE ATT&CK framework. MDE empowers your enterprise to rapidly stop attacks, scale your security resources and evolve your defences by delivering best-in-class endpoint security across Windows, macOS, Linux, Android, iOS and network devices.
Keeping your business safe is your number one priority. It’s ours too. Fusing advanced detection technologies with deep forensic expertise, we help you join all the dots to rapidly distil threats. Our innovative solutions give you the confidence and proactive control you need – whatever comes your way. We’re here to help you keep your people and your reputation safe 24x7. It’s what we do for companies around the world every day.
With Cyberseer, you’re no longer on your own.
If you would like to know more about our Managed Security Service or the advanced technologies that we use, then please get in touch.

Stay ahead of evolving cyber threats. Download the H1 2025 Cyberseer SOC Threat Findings Report for insights on AiTM phishing, malware persistence, and more.