After a quick browse of cybersecurity headlines, any reader would quickly see the sheer volume of new and evolving threats an organisation may face. Often the biggest threats originate from outside an organisation. However, inside threats such as employee data theft with work-related data should be treated with just as much urgency.
Whether you are a large, medium or small-sized organisation, employee data theft is a huge problem that needs to be identified as early as possible. Not so long ago an employee data theft breach could be wrapped up and escape news headlines, however, with the introduction of GDPR and strict guidelines on reporting such breaches, this is no longer the case.
Employee Data Theft Motive
Motives for insider data theft can range from career development to deliberate theft to cause damage. Intellectual property (trade secrets and financial forecasts) and Personally Identifiable Information (PII) can be extremely valuable to the right buyer. Citing the 2018 Verizon Data Breach Report [1], 76% of data breaches in 2017 were linked to an individual stealing data for financial gain.
Take the following scenario - An employee hands in their resignation and during their notice period they most likely still have access to important systems and file shares to carry out their day-to-day work. It only takes them a number of minutes to transfer sensitive files to their local machine and then to a USB stick. As an organisation, how can you get the visibility to detect such an event?
Recently at a customer who has deployed an advanced network traffic monitoring solution, Cyberseer’s Analysts noticed suspicious user activity where an employee connecting to and downloading a large number of files from an internal file share.
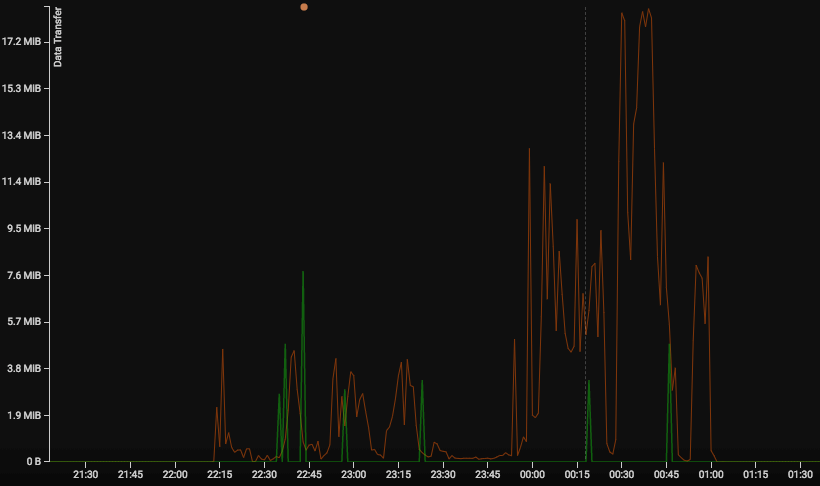
Upon alerting the customer, it was revealed that this employee was mid-way through their notice period after recently handing in their resignation. As a figure with a senior position, they had access to business accounts information, contracts and internal payroll data. Stepping back and looking at the incident timeline and insider threat indicators, it went as follows:
- The remote user connects to the corporate network via VPN -
Their credentials are tracked and an out-of-hours connection is seen as abnormal when compared to the user’s daily activity.
- The user connects to file share -
An unusual time for connection to file share when compared to the user’s history.
- The user begins transferring large numbers of files to the local machine -
An unusual amount of data is transferred when compared to the user’s history.
When?
Detecting employees committing data theft in your organisation's network can be challenging. It's impossible to get inside the heads of your employees and equally as hard to know when they are planning to resign. Rather than waiting to be made aware of an employee's resignation in order to become a high-risk, think about deploying the right cybersecurity software solutions that provide full visibility into your network and continuously monitor all users and devices to look out for the early signs of compromise.
Sources: [1] - https://www.verizonenterprise.com/resources/reports/rp_DBIR_2018_Report_execsummary_en_xg.pdf
