Cyberseer deploys advanced threat detection solutions as part of its managed security services across various businesses and industries. However, suites of advanced tools can only complement but never replace human expertise and knowledge of the intricacies of technology.
This was reflected to us again recently when one of Cyberseer’s clients was hit with an attempted brute force of an executive user. This activity was discovered using Whois tools and promptly reported by the Cyberseer SOC (Security Operations Centre) team to the client, resulting in further investigation by both Cyberseer and the client.
Discussions with the client resulted in both parties discovering that geolocation tools were tracking the IP to the following locations:
- Bratislava, Slovakia - ISP Neterra ltd
- North Holland, Amsterdam - ISP Delis LLC (Organisation Des Capital)
- South Holland, Brielle - ISP Delis LLC (Organisation Des Capital)
- Ashburn, United States - ISP Delis LLC (Organisation Des Capital
This became an interesting problem for us as accurate IP Geolocation is essential in performing accurate open-source intelligence collection. One incorrect step can result in the remaining information being incorrect, therefore also making the context surrounding the incident potentially incorrect.
The initial spot by Cyberseer was this IP's use of a "maintainer" for its Whois infrastructure, illustrated in action in the screenshot below:
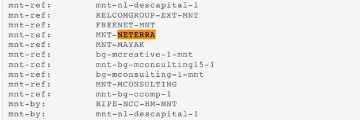
Maintainers are used for securing an object against deletion in large-scale Whois infrastructure such as RIPE. The establishment of a maintainer ensures that only authorised people who have access to the maintainer can change other objects that are protected by the maintainer. It appears that some services are mis-parsing the record and choosing Neterra as the ISP due to this; Neterra has a presence in Slovakia - hence the Bratislava location.
Regarding the other chosen providers, Delis LLC appears to be a hosting provider for the ISP Des Capital. The specific Des Capital subnet that our IP is from, does, in fact, appear to be in the Netherlands.
On the topic of the US attributions - the contact listed for the service is specified to be in Dover, US. So, this still doesn't explain Ashburn. The services that indicate that the address could be in Ashburn both have tools for reporting out-of-date data, and both even specify a postal code for the address. The screenshot below indicates the latest US contacts for Delis (taken from the Whois record today) so I would judge that these services are operating with historical data for the company.
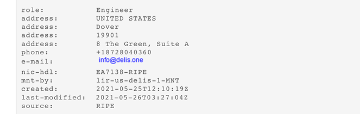
This manual work allowed both Cyberseer and the client to confirm that the address was based in the Netherlands and move forward to mitigate the risks posed by this attack. Having accurate information regarding the IP of the bad actor resulted in the executive account remaining secure and data remaining protected.
If you have any questions or wish to discuss how Cyberseer’s SOC service can assist you further, then please do get in touch.
