21 months after WannaCry's initial discovery, a recent report from Kaspersky Labs has revealed that the WannaCry ransomware is still the most prevalent “crypter” with close to 75,000 users being infected as of Q3 2018, more than double that of its closest rival [1]. More worrying however is that between Q3 of 2017 and Q3 of 2018, the number of WannaCry attacks increased by about two-thirds.
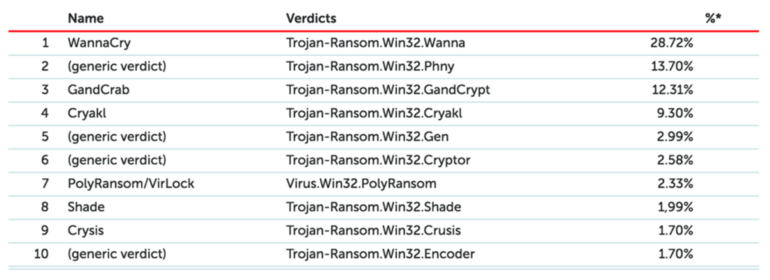
Figure 1 - Most popular Crypters [1]
WannaCry spreads via the use of the EternalBlue exploit, a leaked NSA hacking tool that incorporated worm-like capabilities to scan internal devices, exploit them and then install another NSA tool DoublePulsar that acts as a backdoor. The self-propagating nature of the exploit has meant that WannaCry has never slowed down in attempting to spread itself after first being unleashed.
Case Study
Recently a Cyberseer client was unexpectedly hit by the attack. Luckily they were not impacted by the crypter, and the propagation through the network was detected and alerted by Cyberseer Analysts.
Following the initial compromise, a device was seen scanning the network in an attempt to locate other devices open to SMB connections:
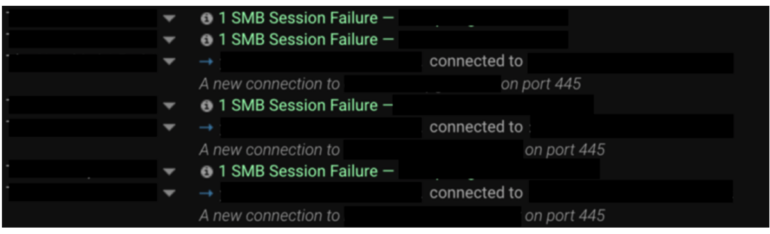
Figure 2 - Internal SMB connections
The worm initially scans the network to identify if the DoublePulsar backdoor is already present and if so the ransomware can be dropped. If the backdoor is not found, the EternalBlue exploit is used to infect and then install both WannaCry and the DoublePulsar backdoor. This can be verified by looking at a packet capture of the event:
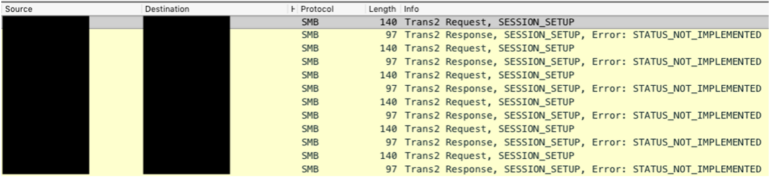
Figure 3 - Device scanning to check if the target Windows system is already exploited or not
Exploited devices were then observed scanning both internally and externally on port 445:
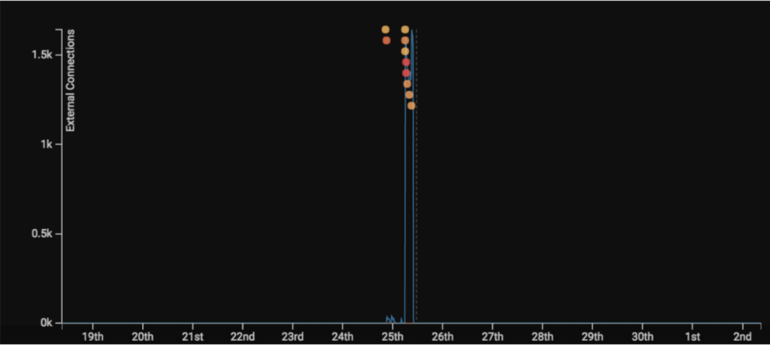
Figure 4 - Graph showing a spike in external connections and associated model breaches
Quick takeaways
Despite the WannaCry attacks reaffirming the importance of patching, the EternalBlue vulnerability that the ransomware leverages was addressed by Microsoft almost two months before the attack. The unrelenting infections and damage caused demonstrate many organisations are still vulnerable and at risk. Path management is still a key component of an effective security posture, as is the ability to recover lost files should the business be hit by ransomware.
Sources: [1] securelist.com
