
Interested in SOC Services for Darktrace?
Enhance your cybersecurity posture and embrace the future of threat detection with Cyberseer's SOC services for Darktrace.
Cyberseer deploys advanced threat detection solutions as part of its managed security services, across a range of businesses and industries. Recently, one of Cyberseer’s clients was hit with a phishing campaign aiming to plant the Dridex malware within its network.
While the client’s e-mail gateway blocked 90% of the e-mails, in certain scenarios the phishing messages were able to bypass filters and reach their targets. The majority of users who received the e-mail were cautious and did not click the embedded hyperlink. One user, however, was not so vigilant and downloaded the malicious Windows executable file.
At the time the file was downloaded, mainstream malware databases had no records for the file’s MD5/SHA256 hashes, and all of the client’s traditional security defences failed to detect or block the Dridex Trojan.
By leveraging Darktrace Detect, a machine learning and mathematics-driven cyber defence immune system, Cyberseer Analysts were able to rapidly detect and alert the customer to the breach, and prevent further infection and network disruption.
Dridex is a banking Trojan designed to compromise a victim’s computer to steal sensitive and personal information. The Dridex malware’s main objective is to steal banking credentials which can then be used to siphon funds from the victim’s bank accounts.
The Dridex malware strain was first identified in late 2014 by Symantec [1] and since has been subject to an international crackdown led by the National Crime Agency in collaboration with the FBI. The operation led to the arrest of a Moldovan suspect who was believed to run the command and control centre for Dridex.
During its initial campaign, Dridex was thought to be responsible for the theft of over £20 million from infected users’ bank accounts [2]. While the arrest of the suspected operator initially led to a reduction in the number of spam campaigns and infection sources, during January 2016 the Dridex malware campaign appeared to return to full force. The graph from Fire Eye [3] below shows an enormous spike in detections, for this period:
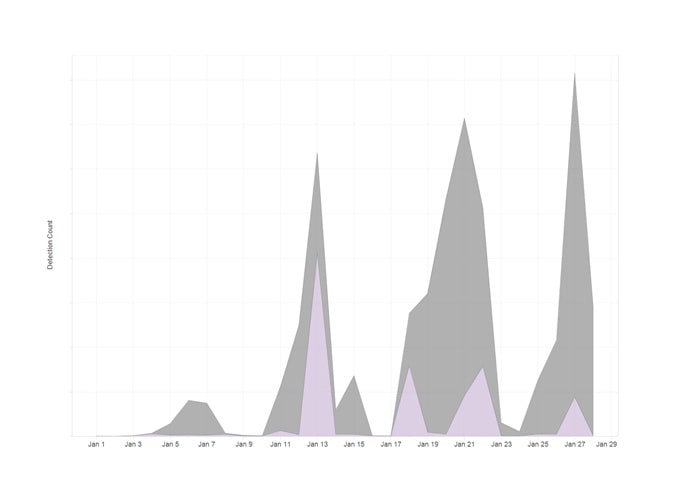
The Dridex Trojan has been seen largely targeting manufacturing, telecommunications, and financial services sectors, and is often distributed through malicious e-mails sent by criminal operators.
A number of delivery techniques have been identified, ranging from malicious Macro downloaders hidden within Excel (.xls) and Word (.doc) documents to embedded JavaScript which redirects a user to download a file from a website.
In the attack scenario detected by Cyberseer, the user was tricked into clicking a hyperlink to download a malicious binary from the attacker’s website. Following this malicious download, the malware is installed and the machine is compromised.
Signature-based threat detection techniques were unable to detect this instance of Dridex, as the current phase of the malware campaign introduced new iterations of the malware which had not been seen previously, and meant that effective signatures were not available.
Darktrace’s Enterprise Immune System, however, does not rely on signatures and has no prerequisites for determining malicious network activity. Utilising machine learning, the Darktrace technology models network traffic to understand normal patterns of activity for users, connections, devices and the network as a whole. Activity that is determined to be ‘unusual’ is flagged for analysis by Cyberseer to determine whether it is a genuine threat.
When the victim clicked on the hyperlink in the Phishing e-mail, their PC made a connection to the internet and downloaded the Dridex binary. Cyberseer Analysts could see the Darktrace technology had captured and processed this connection in real-time, identifying the endpoint as ‘Rare’ and ‘Unusual’:
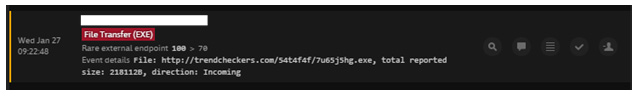
Darktrace alert for the unusual Dridex download.
Cyberseer identified the device connecting to a new rare external endpoint (trendcheckers.com) and downloading an uncommon exe file (7u65j5hg.exe) which was seen as unusual behaviour. As Darktrace is continually capturing network traffic it is possible to generate and analyse packet captures for devices on the network. In this case, Cyberseer used the packet capture to confirm that the Dridex download was successful:

It is also interesting to note this connection was made via a proxy, which failed to identify the connection as malicious.
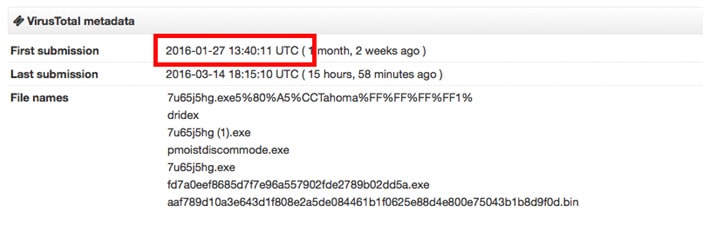
At the time of the alert (09:22 on Jan 27), there was no open-source intelligence for the hash of the specific Dridex binary. The screenshot below shows the malware was uploaded to VirusTotal on Jan 27 at 13:40, approximately 4 hours later:
Following the real-time Darktrace alert, Cyberseer Forensic Analysts were able to rapidly investigate the file and contact the client. The device was successfully quarantined and re-mediated before a further compromise could occur.
 This scenario highlights how traditional signature-based approaches are not enough to adequately defend a network against constantly evolving, new unknown threats. The Darktrace technology does not require any prior knowledge of threats or need to update signature definitions.
This scenario highlights how traditional signature-based approaches are not enough to adequately defend a network against constantly evolving, new unknown threats. The Darktrace technology does not require any prior knowledge of threats or need to update signature definitions.
As shown above, a machine-learnt behavioural approach to security can detect threats ahead of other traditional solutions, allowing a faster response to potential breaches. Security technologies that require signatures and blacklists to be updated will always be one step behind the attackers and never be able to detect new unknown threats in real time.
Cyberseer’s threat detection and analysis service bridges the gaps in an organisation's cyber defence system. Having the ability to detect and understand the severity of internal and external threats provides effective threat mitigation.
Understanding your organisation's threat score and dealing with live issues early, decreases incident response times and significantly reduces the risk of cyber damage.
Sources: [1] Broadcom [2] Finextra [3] Fire Eye

Enhance your cybersecurity posture and embrace the future of threat detection with Cyberseer's SOC services for Darktrace.